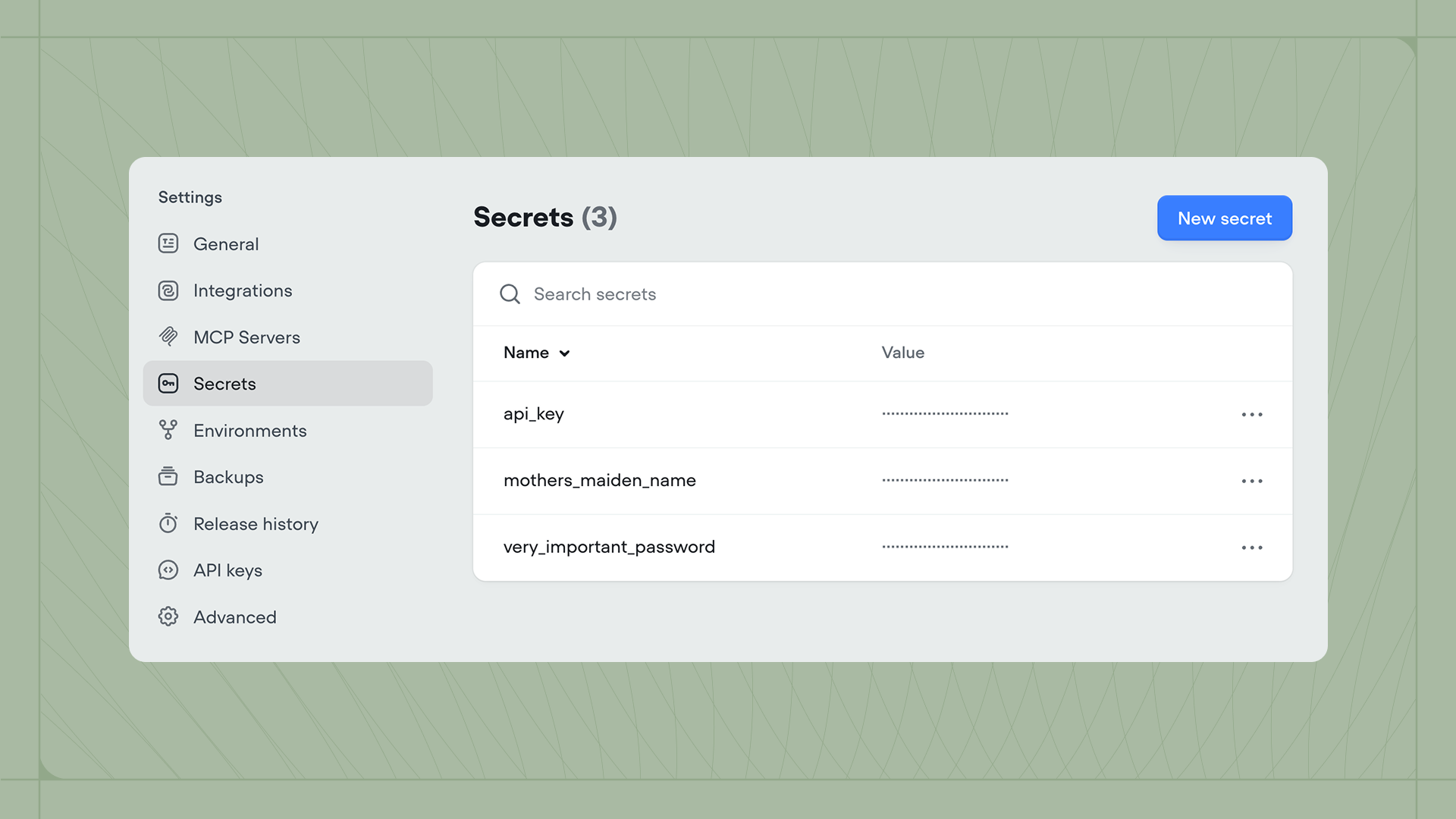
Creating secrets
You can create and manage secrets in Settings → Secrets. Click New Secret in the top right to create one. When creating a secret, you’ll provide a name, value, and visibility setting:- Masked secrets are hidden by default but can be temporarily revealed by clicking on them.
- Restricted secrets cannot be revealed after creation. Use this for highly sensitive credentials.
{ in any input field, switch to the Secrets tab in the dropdown, then click Create Secret at the bottom.
Using secrets
Secrets work like variables but are accessed from a separate tab. In any input field within a tool, type{ to open the dropdown, then switch to the Secrets tab and select the secret you need.
(image)